How to configure Identity Manager
Prerequisites:
- SOLIDServer 7.3+, or 8.0+
- CA Certificate and its key in PEM format.
- (CA signed) SSL Certificate for the management appliance or the pair of management if you have hot standby. The certificate and its private key must be in PEM format.
- (CA signed) SSL Certificate/s for the AD/s in pfx format.
Lab components:
- Management appliance:
FQDN: mgmt.eip.local
IP: 192.168.1.40
- AD Server:
FQDN: ad.eip.local
IP: 192.168.1.44
- Client machines:
FQDN: dp-client-02.eip.local
IP: 192.168.1.61
FQDN: dp-client-04.eip.local
IP: 192.168.1.60
Certificates:
You can use the management SOLIDServer to generate the certificates,
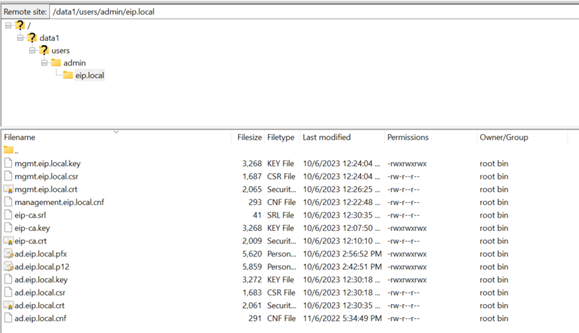
mkdir /data1/users/admin/eip.local
cd /data1/users/admin/eip.local
- CA Certificate:
openssl genrsa -out eip-ca.key 4096
openssl req -x509 -new -nodes -key eip-ca.key -days 3650 -out eip-ca.crt -subj '/C=AE/ST=Dubai/L=Dubai/O=IT/OU=SE/CN=EIP LOCAL CA/'
Copy the CA Thumbprint as it will be required to configure Event Forwarder:
openssl x509 -in eip-ca.crt -fingerprint -sha1 -noout | sed -e 's/\://g'
Output:
sha1 Fingerprint=943A5FA37BD19C61F0B60D7BE51A42901BBC87DA
- MGMT Certificate:
ee mgmt.eip.local.cnf
openssl req -new -newkey rsa:4096 -nodes -out mgmt.eip.local.csr -keyout mgmt.eip.local.key -subj '/C=AE/ST=Dubai/L=Dubai/O=IT/OU=SE/CN=mgmt.eip.local/'
openssl x509 -req -in mgmt.eip.local.csr -out mgmt.eip.local.crt -CA eip-ca.crt -CAkey eip-ca.key -CAcreateserial -extfile management.eip.local.cnf -extensions req_ext -days 365
- EIP Certificate:
ee ad.eip.local.cnf
openssl req -new -newkey rsa:4096 -nodes -out ad.eip.local.csr -keyout ad.eip.local.key -subj '/C=AE/ST=Dubai/L=Dubai/O=IT/OU=SE/CN=ad.eip.local/'
openssl x509 -req -in ad.eip.local.csr -out ad.eip.local.crt -CA eip-ca.crt -CAkey eip-ca.key -CAcreateserial -extfile ad.eip.local.cnf -extensions req_ext -days 365
openssl pkcs12 -export -certpbe PBE-SHA1-3DES -keypbe PBE-SHA1-3DES -nomac -inkey ad.eip.local.key -in ad.eip.local.crt -certfile eip-ca.crt -out ad.eip.local.pfx
When asking for an exporting password, keep it empty.
You can use FileZilla to download the certificate:
Configurations from EIP side:
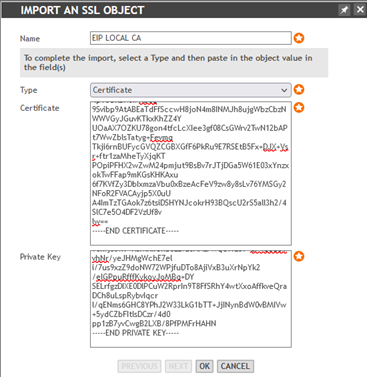
1. Upload the CA certificate and key to the management appliance.
eip-ca.crt + eip-ca.key
- Upload the SOLIDServer certificate and key to the management appliance.
mgmt.eip.local.crt
mgmt.eip.local.key
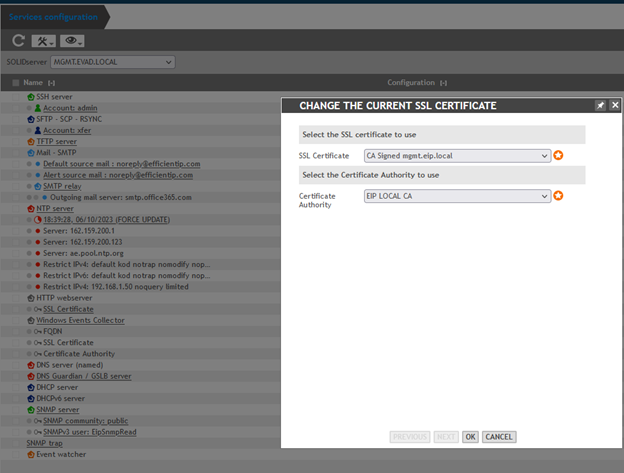
- Select the CA and SSL certificates in the Windows Event Forwarder
4. Make sure the rule 116 is enabled in the firewall: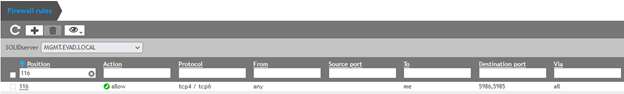
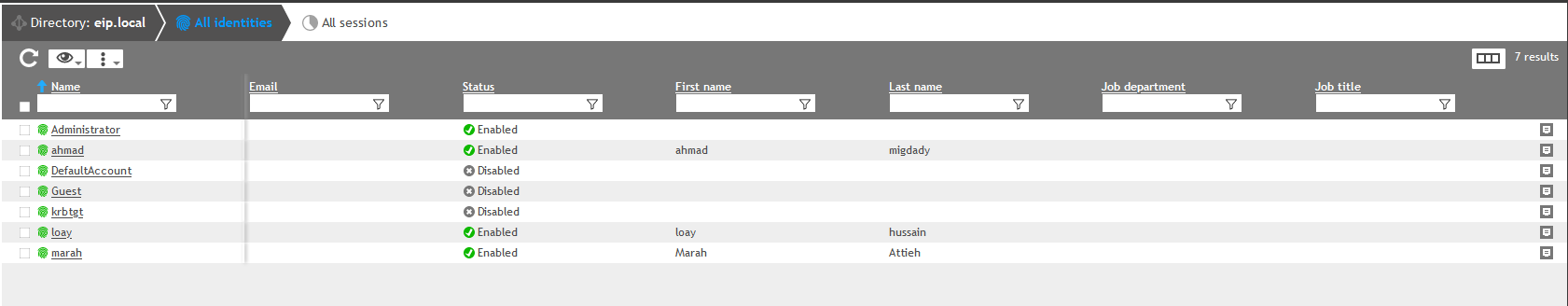
5. Create ID Manager Directory named after your domain: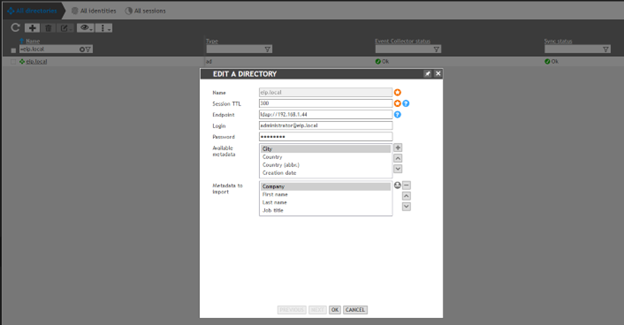
Configurations from AD side:
- Allow the port 5986 TCP towards EIP management appliance/s.
- From a terminal, configure Windows Remote Management to enable authentication via certificate using the following commands:
winrm qc -q
winrm set winrm/config/client/auth @{Certificate="true"}
- Import the AD pfx certificate (ad.eip.local.pfx), to the local computer certificate, The file must contain the public and private information of the SSL certificate for the domain controller and the public information of the CA. The same CA was imported in SOLIDserver.
Keep the password empty and import.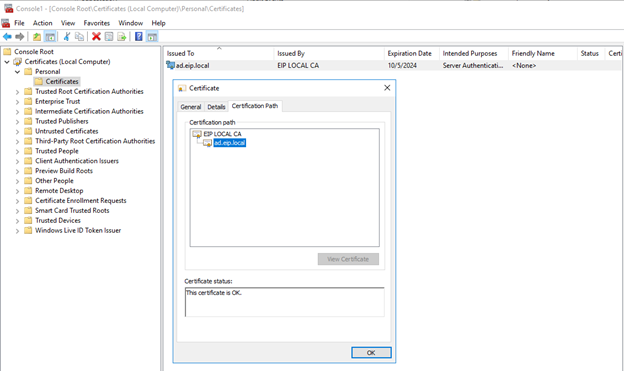
right click on the imported certificate>>All Tasks>> Manage Private Keys.
Grant full control to the NETWORK SERVICE
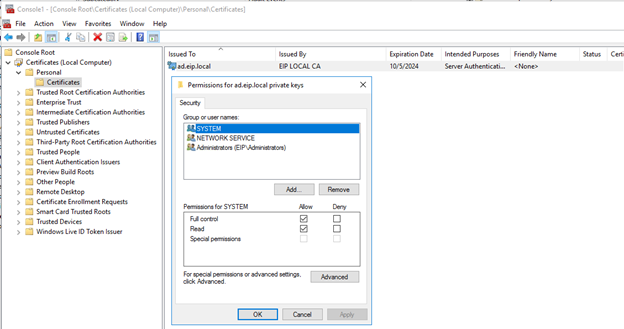
- Open (gpedit.msc), and configure the source host security policy to enable event forwarding.
Computer Configuration > Administrative Templates > Windows Components >Event Forwarding.
Configure target subscription Manager:
server=https://mgmt.eip.local:5986/wsman/,Refresh=60,IssuerCA=943A5FA37BD19C61F0B60D7BE51A42901BBC87DA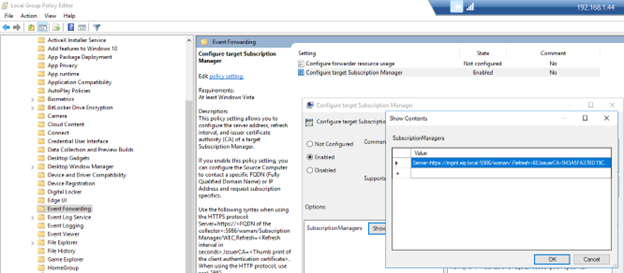
Note: the IssuerCA = Thumbprint of the CA certificate. - gpupdate /force
- open Active directory users and computers, authorize the forwarding of security logs to the NETWORK SERVICE account.
Under Builtin, Event Log Readers >> Properties>> Members>> NETWORK SERVICE. - Reboot the AD.
- If several AD domains controllers manage the AD domain and you want to monitor from SOLIDserver, you must repeat the steps on each controller.
Once the event forwarding is configured on all relevant AD domain controllers, you must configure the log generation. This configuration applies to all related AD domain controllers.
- gpedit.msc.
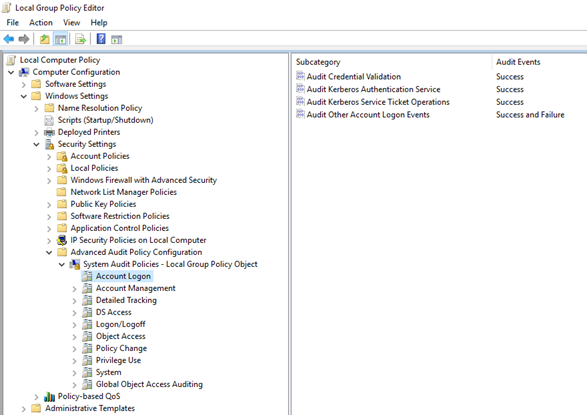
- Computer Configuration > Windows Settings > Security Settings > Advanced Audit Policy Configuration > System Audit Policies > Account Logon and configure the following:
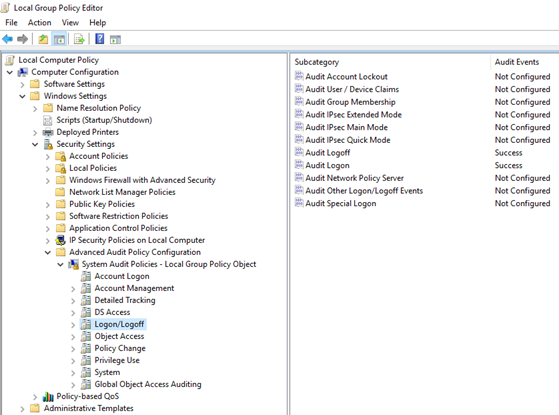
- Go to Computer Configuration > Windows Settings > Security Settings > Advanced Audit Policy Configuration > System Audit Policies > Logon/Logoff and configure the following:
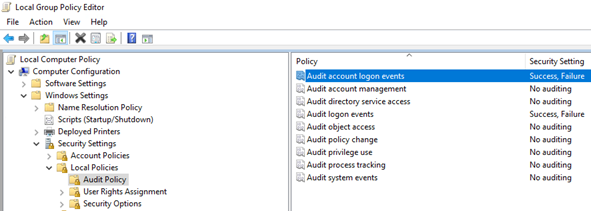
- gpupdate /force
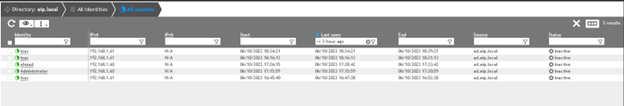
- Login to the client machine using a domain user.
- From SOLIDServer
NTP force, and check the logs:
tail -f /var/log/http-access.log | grep 192.168.1.
Check the logs from AD:
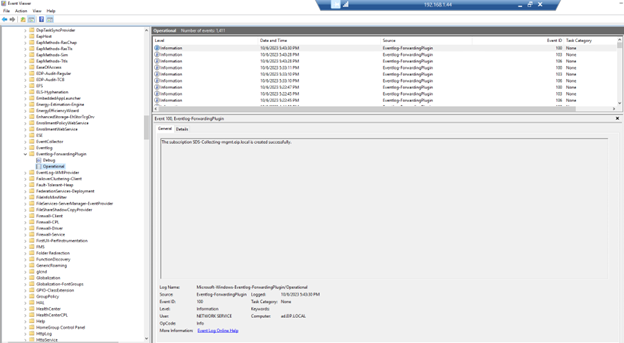
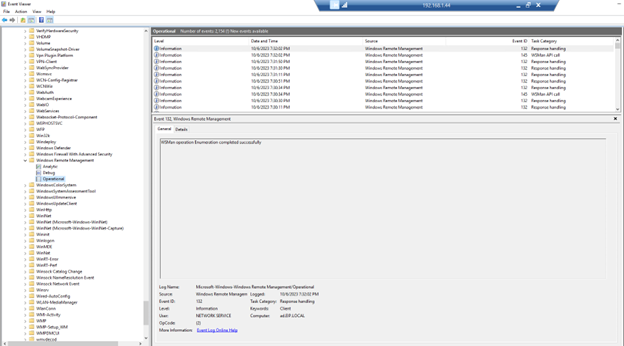
Event viewer >> application and services logs>> Microsoft>> Windows>> Windows Remote Management